Crypto Address Poisoning Scams Steal $1.6M in a Week — Largest Spike This Year
-
Scammers using crypto address poisoning tactics netted more than $1.6 million from unsuspecting users this week — surpassing total losses for the entire month of March, according to alerts from ScamSniffer and Web3 Antivirus.
Million-Dollar Losses in Days
Friday: One victim lost 140 ETH (~$636,500) after sending funds to a lookalike address embedded in their wallet’s transaction history.
Sunday: Another victim lost $880,000 in USDT in a similar attack.
Other cases this week include individual losses of $80,000 and $62,000.
ScamSniffer says the $636K victim’s history was “full of poison address attacks,” making it “only a matter of time before the trap worked.”
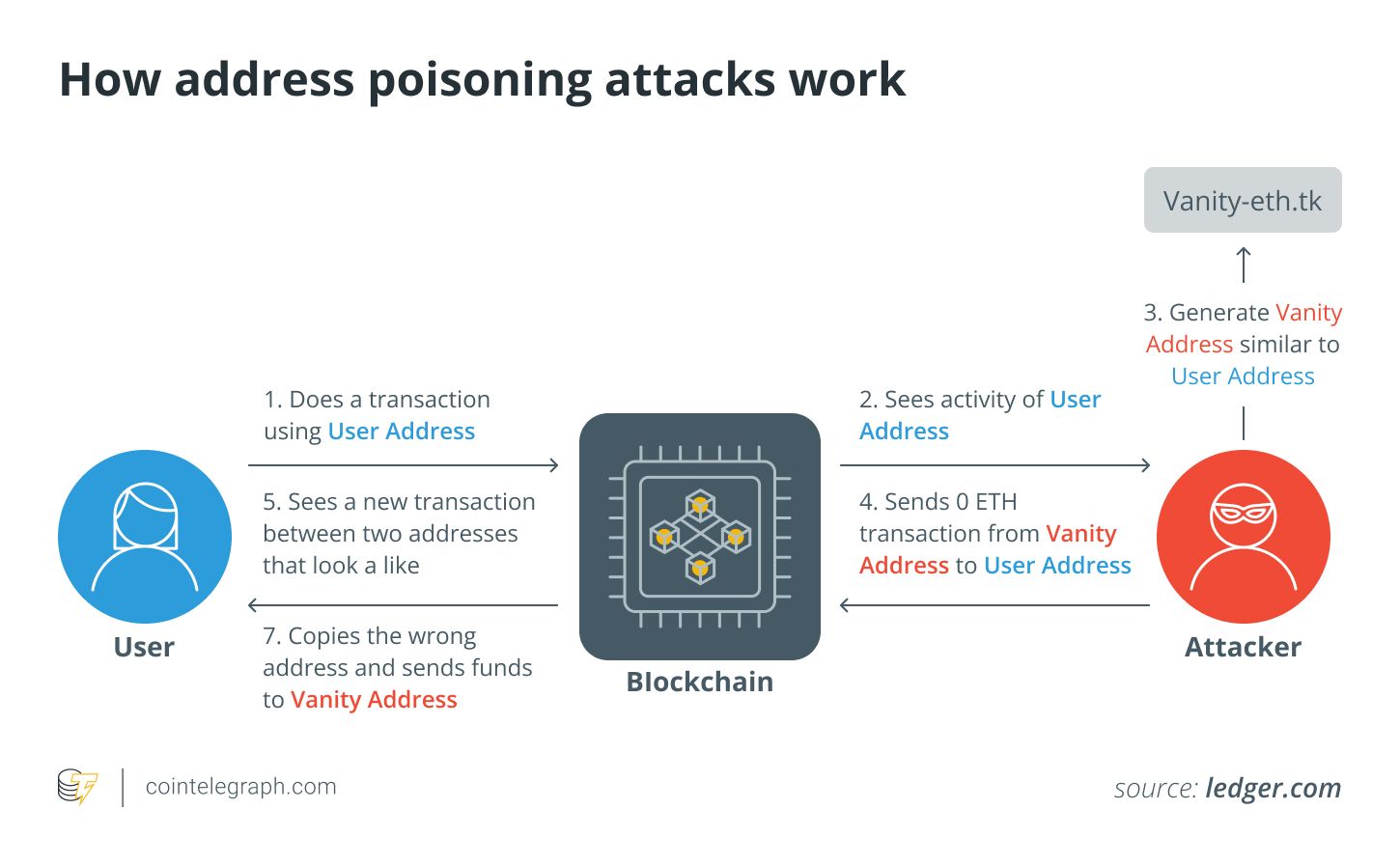
How Address Poisoning Works
Address poisoning exploits human copy-paste habits:
Scammer sends a tiny transaction from an address that closely resembles a legitimate one.
The fake address appears in the victim’s transaction history.
When the victim later copies it for a payment, the funds are sent to the attacker.
“Poisoners send small transfers from addresses that mimic a real one, so copying from history becomes a trap,” said Web3 Antivirus.
Phishing Signatures Compound Losses
On top of address poisoning, scammers also stole $600,000+ this week through malicious signature requests — tricking victims into signing “approve,” “increaseAllowance,” and “permit” transactions.
Tuesday: One victim lost $165,000 in BLOCK and DOLO tokens after approving a malicious signature.
Security Warnings
Experts stress:
Never copy wallet addresses from transaction history — use an address book or whitelist.
Verify the full address before sending, not just the first/last characters.
Treat unsolicited signature requests as suspicious.
“We sound like a broken record, but it’s worth mentioning again,” wrote Web3 Antivirus.
Bottom line: Address poisoning is surging, and attackers are pairing it with phishing signatures to drain wallets faster. With over $1.6M stolen in under a week, this vector is now one of the most dangerous active scams in Web3.
-
This is one of the scariest examples of how simple habits can cost people life-changing money. Address poisoning isn’t even a sophisticated hack — it’s just social engineering that exploits the way most users copy-paste from history. The fact that one wallet had its entire transaction list filled with poison attempts shows how relentless these scammers are. Once you’re rushing or distracted, it only takes one wrong copy for hundreds of thousands to vanish. People really need to start using address books, whitelists, or ENS domains instead of relying on memory and history. It might feel like overkill, but after seeing $636K vanish in one click, prevention suddenly looks cheap.
-
What’s especially concerning is how attackers are now stacking exploits: poisoning + phishing signatures. It means even vigilant users can get caught — maybe they verify an address, but then approve a malicious “permit” request and lose everything anyway. The pace of these attacks is insane: $1.6M in days, not months. The lesson is clear: in Web3, speed kills — rushing through a transfer or signature is what scammers are counting on. Triple-check the full address, reject anything you didn’t initiate, and remember: wallets don’t need “approval” for random tokens out of nowhere. The more the ecosystem educates about these traps, the harder it will be for scammers to keep winning at this scale.

















