🚨 North Korean IT Workers Infiltrate Crypto Projects via Fake IDs & Google Tools
-
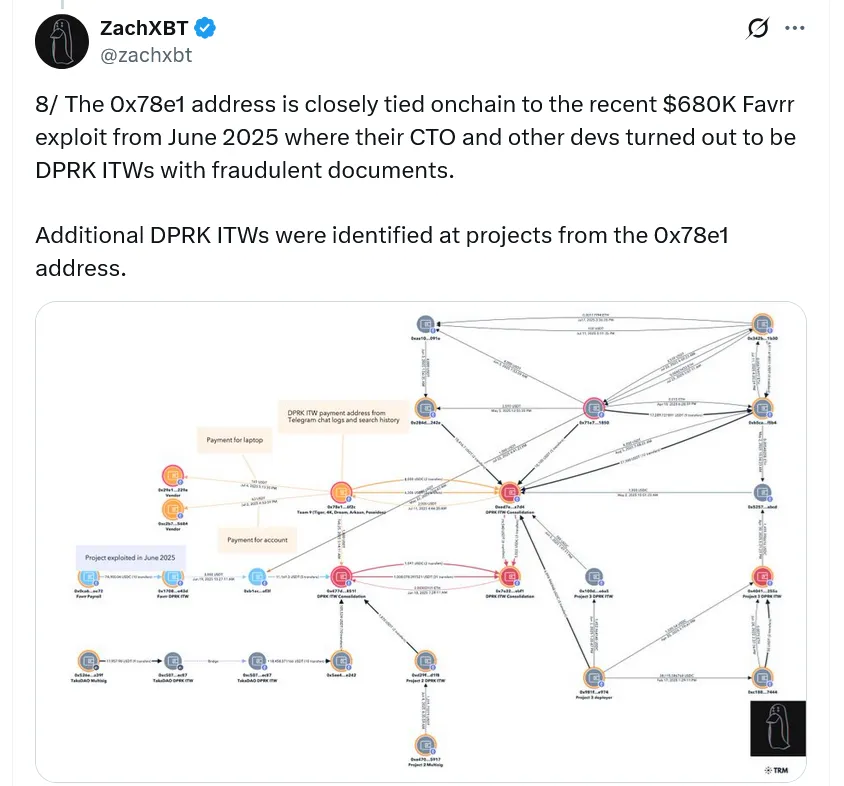
A small DPRK team linked to a $680K crypto hack in June has been exposed using fake identities, Google products, and freelance platforms to penetrate the Web3 industry. ️ Key findings (via @zachxbt):
️ Key findings (via @zachxbt):The six-person team used at least 31 fake identities with real government IDs, phone numbers, and purchased Upwork/LinkedIn accounts.
Posed as engineers from Polygon Labs, OpenSea, and Chainlink in scripted interviews.
Secured jobs on Upwork as blockchain devs, accessed companies using AnyDesk, VPNs, and Google tools for ops and comms.
Monthly expenses to run the op: $1,489 (as shown in internal docs).
Tied to $680K exploit on Favrr in June 2025 via wallet 0x78e1a.
Used Payoneer to convert fiat to crypto.
 Leaked docs show:
Leaked docs show:Interview prep docs.
Curiosity in AI firms and ERC-20 deployment on Solana.
Chrome profiles, Google Drive exports, and budget spreadsheets in English via translation tools.
🧠 Why it matters:
DPRK ops aren’t always sophisticated, just persistent.
Lax hiring and minimal due diligence = big vulnerabilities.
U.S. Treasury recently sanctioned multiple actors linked to similar rings.
 Takeaway for crypto orgs:
Takeaway for crypto orgs:
Stronger due diligence and better platform coordination are urgently needed. -
What’s striking here is how low-budget yet effective this op was — under $1.5K/month in expenses to infiltrate legitimate companies and pull off a $680K heist. That should be a massive wake-up call for Web3 teams: these aren’t elite cyberwarfare units every time, they’re small, persistent groups exploiting the weakest link — human trust. The fake LinkedIn and Upwork angles are especially worrying, because they bypass traditional “tech” defenses entirely. Even the best code audits won’t help if the attacker is inside your Slack and repo.
-
The bigger issue isn’t just DPRK’s tactics — it’s how many hiring pipelines in Web3 are wide open for this kind of abuse. Contract-to-hire without serious vetting, outsourced HR with no blockchain-specific security training, and zero cross-platform data sharing between LinkedIn, Upwork, and exchanges means bad actors can keep recycling identities. Until there’s industry-wide due diligence standards — identity verification, wallet history checks, and platform-to-platform alerts — we’ll keep reading the same headlines. The technology may be decentralized, but security coordination needs to be far more centralized.

















