💻 Ransomware Group “Embargo” Linked to $34M in Crypto Since April
-
A relatively new ransomware outfit called Embargo has quickly become a major cybercrime player — moving over $34M in crypto-linked ransom payments since April 2024, according to blockchain intel firm TRM Labs.
 How They Operate
How They OperateModel: Ransomware-as-a-Service (RaaS) Tactics: Double extortion — encrypt systems + threaten to leak data Targets: High-cost downtime sectors (healthcare, manufacturing, business services) Focus: Primarily U.S. victims with higher ability to pay Known Victims
Known VictimsAmerican Associated Pharmacies Memorial Hospital and Manor (Georgia) Weiser Memorial Hospital (Idaho) 💰 Ransom demands: up to $1.3M Possible BlackCat Connection
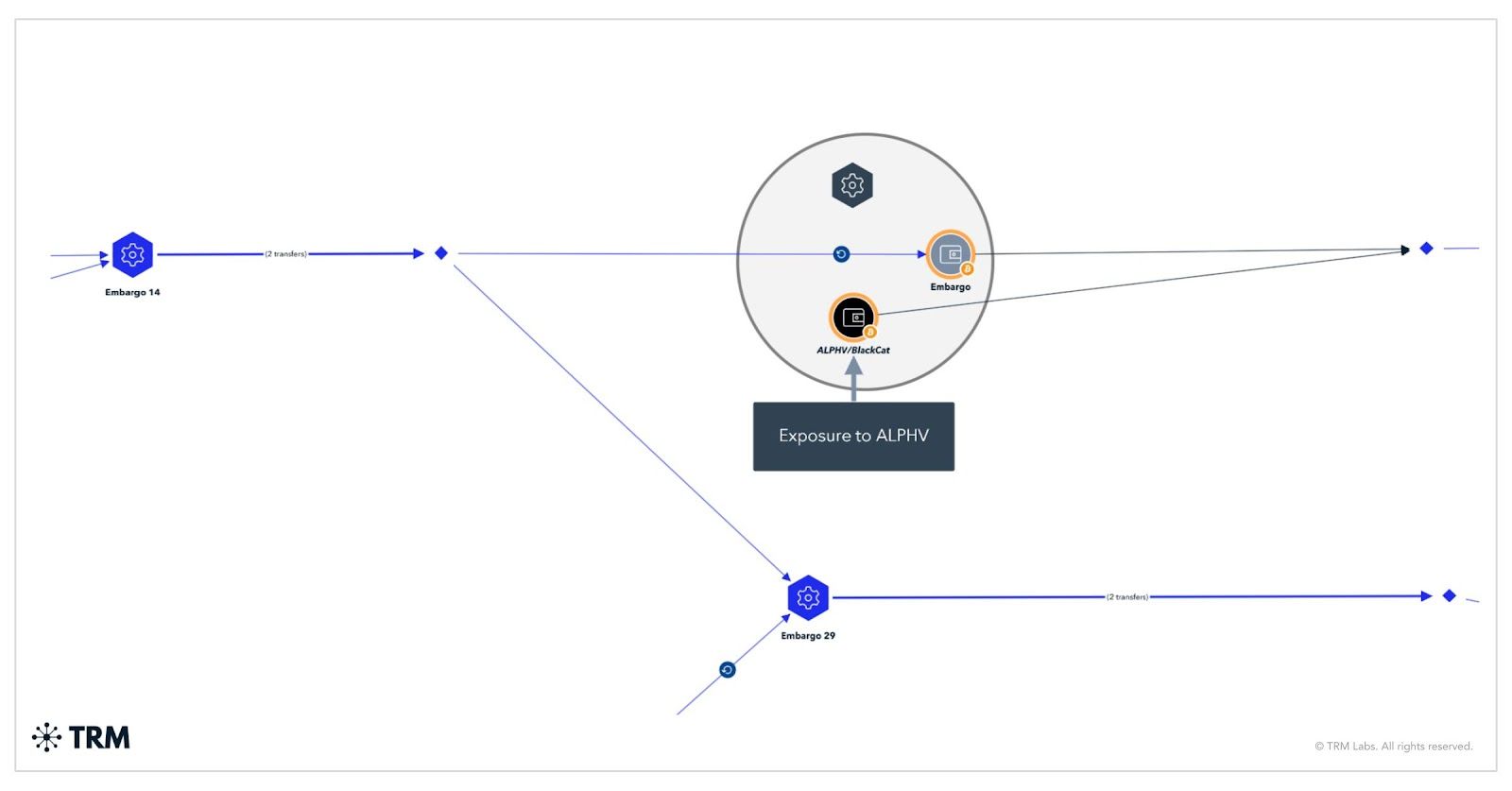
Possible BlackCat ConnectionTRM suspects Embargo could be a rebrand of BlackCat (ALPHV) — which vanished earlier this year in a suspected exit scam.
Similarities include:Rust-based ransomware Nearly identical leak sites On-chain wallet overlaps Money Trail
Money Trail$18.8M in dormant crypto in unaffiliated wallets (possibly waiting for laundering opportunities) Funds moved through high-risk exchanges & sanctioned platforms like Cryptex.net May–Aug: $13.5M traced through various providers; $1M+ via Cryptex Policy Moves
Policy MovesThe UK plans to ban ransomware payments for all public sector & critical infrastructure operators.
Key points:Mandatory reporting within 72 hours + detailed follow-up in 28 days Prevention regime for victims outside the ban Comes after ransomware revenues dropped 35% last year (Chainalysis data) Takeaway:
Takeaway:
Embargo isn’t yet as aggressive as LockBit or Cl0p, but it’s carving out a niche by hitting sectors where downtime is expensive — and its suspected BlackCat ties suggest a seasoned team behind the scenes.

















