🚨 CrediX Recovers $4.5M in Crypto After Striking a Deal with Hacker 💼
-
In a rare win for crypto investors, CrediX has successfully recovered $4.5 million in stolen crypto after negotiating directly with the hacker behind this week’s exploit.
 ️
️ ️ The attacker, who used Tornado Cash to mask their movements, agreed to return the full amount in exchange for an undisclosed bounty paid from the CrediX treasury.
️ The attacker, who used Tornado Cash to mask their movements, agreed to return the full amount in exchange for an undisclosed bounty paid from the CrediX treasury. CrediX confirmed that affected users will receive a refund via airdrop within the next 48 hours.
CrediX confirmed that affected users will receive a refund via airdrop within the next 48 hours.
🧠 What You Need to Know:Hacker returned the funds in a private deal. No official word yet on whether this was labeled a “white hat” bounty. The exploit initially saw funds bridged to Ethereum and obscured through Tornado Cash. Blockchain sleuths were closing in—SlowMist traced IPs possibly linked to Hong Kong, adding pressure. Why It Matters:
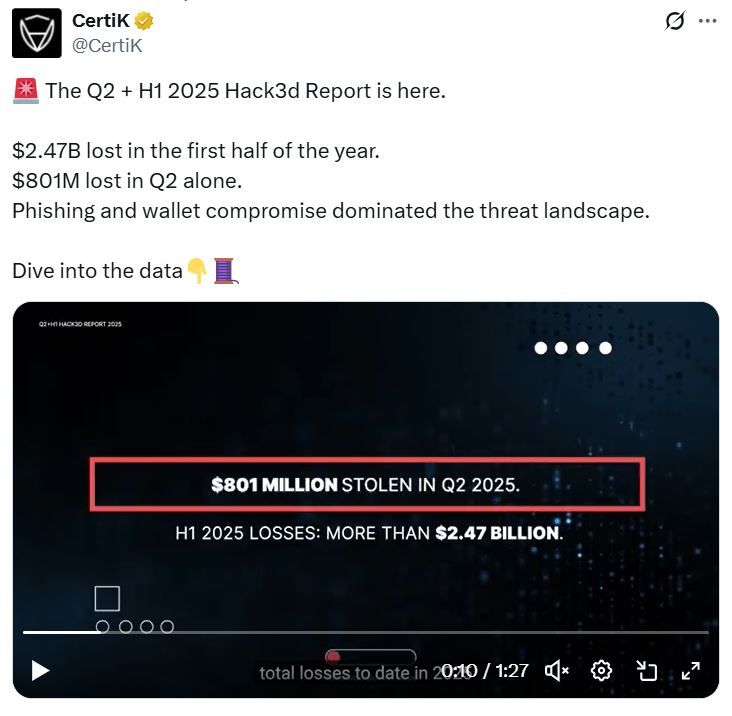
Why It Matters:Crypto thefts are up $2.47B in 2025, and in most cases, the funds are gone for good. But deals like this one (and the recent $40M GMX exploit return) show that negotiation—and public pressure—can pay off.
⚠️ Reminder: Over 80% of tokens never recover in value post-hack. But prompt action and transparency can preserve trust and even reverse the damage. Takeaway: If your project gets hit, staying quiet won’t save you. Transparency, negotiation—and maybe even a bounty—might just bring your crypto home.
Takeaway: If your project gets hit, staying quiet won’t save you. Transparency, negotiation—and maybe even a bounty—might just bring your crypto home.  ️
️ -
This kind of resolution shows just how unique the crypto space is. In traditional finance, recovering stolen funds through a direct deal with the hacker would be nearly impossible — but in Web3, the line between black-hat and white-hat can sometimes blur.What’s more interesting is how these recoveries are often faster than court cases. It highlights the growing importance of on-chain forensics, community pressure, and open negotiation in decentralized environments. Wild story — and a win, even if unconventional. 🧠

-
Glad to see Credix recovered the funds, but this also raises deeper questions: why are these exploits still so common? And should negotiating with hackers become an accepted practice?It’s a slippery slope — while recovery is good, it can also encourage future exploits if attackers think they can walk away with a bounty. That said, the quick resolution here is impressive, and it shows that rapid-response protocols in crypto are evolving fast. Props to the team for damage control.
 ️
️ ️
️ ️
️ ️
️

















