🚨 The 2025 Favrr Heist: How North Korean Operatives Infiltrated Crypto From the Inside
-
In June 2025, fan-token marketplace Favrr fell victim to a $680,000 exploit. At first glance, it looked like just another crypto hack. But when one of the attackers’ devices was counter-hacked, investigators uncovered something far more chilling.
 ️ The Discovery
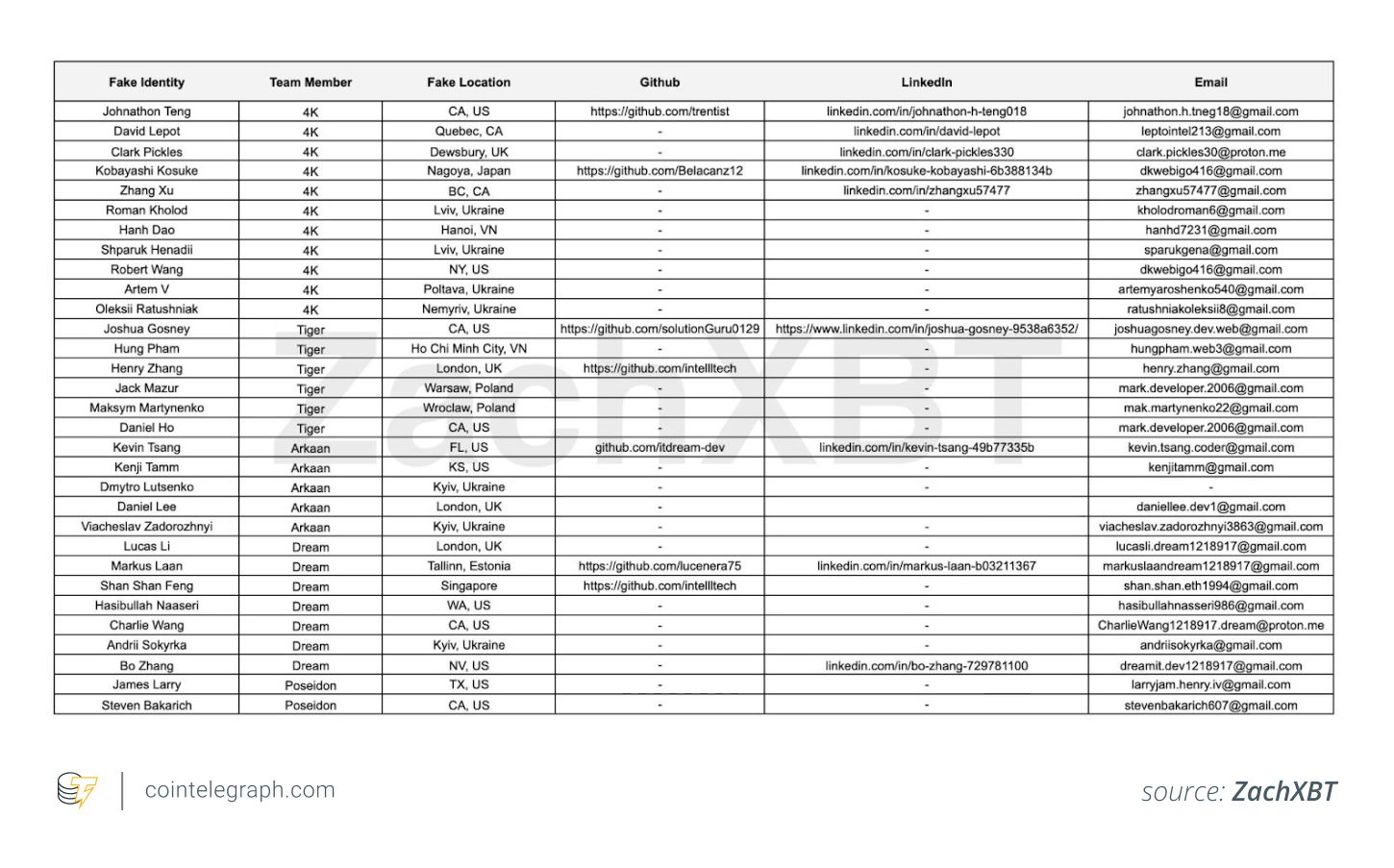
️ The Discovery6 North Korean operatives were running 31 fake identities.
They forged government IDs, phone numbers, and even LinkedIn & Upwork profiles.
Some posed as Polygon Labs, OpenSea, and Chainlink developers to secure remote jobs inside the industry.
Their playbook included Google Drive spreadsheets, Chrome profiles, and even rented hardware — with English smoothed over by Google Translate.
Blockchain sleuth ZachXBT then traced the onchain flows, tying one wallet address directly to the Favrr exploit.
 Deepfake Developers
Deepfake DevelopersThese weren’t your average scammers. The operatives had:
Pre-written interview scripts for fake personas.
Remote job placements that gave them direct access to wallets & systems.
VPNs, AnyDesk, and rented computers to mask their tracks.
This wasn’t phishing — it was full-scale infiltration through remote work infrastructure.
 The Bigger Picture
The Bigger PictureNorth Korea-linked groups stole $1.34B in 2024, about 60% of global crypto thefts.
They often combine brazen exchange hacks (like Lazarus Group’s $1.5B Bybit exploit) with stealthy insider infiltration.
Experts estimate 8,400 operatives worldwide pose as remote blockchain workers, funneling stolen funds back to Pyongyang’s weapons program.
 ️ Why It Matters
️ Why It MattersThe Favrr heist shows the future of cybercrime isn’t just malware — it’s identity-level infiltration.
Fake developers. Fake resumes. Real theft.For crypto companies, this means:
Background checks aren’t enough.
Remote hires must be verified beyond documents.
Onchain forensics & wallet monitoring are now mandatory defenses.
 Takeaway: The 2025 Favrr case isn’t just a $680K hack — it’s proof that state-backed cybercrime has evolved into something corporate-like, methodical, and disturbingly effective.
Takeaway: The 2025 Favrr case isn’t just a $680K hack — it’s proof that state-backed cybercrime has evolved into something corporate-like, methodical, and disturbingly effective.

















