📵 SIM Swap Scams: The Silent Killer of Crypto Wallets
-
Vigilance is often touted as the first line of defense in crypto. But sometimes, even the most guarded practices can collapse in the face of social engineering.
Consider this chilling story:
A crypto investor boarded a red-eye flight. Minutes after takeoff, his phone went dark — just another “no-signal” moment, or so he thought. By the time he landed, his wallet had been drained. While he was offline, attackers had hijacked his phone number, intercepted his 2FA codes, and taken control of his exchange account.
Welcome to the world of SIM swap scams.
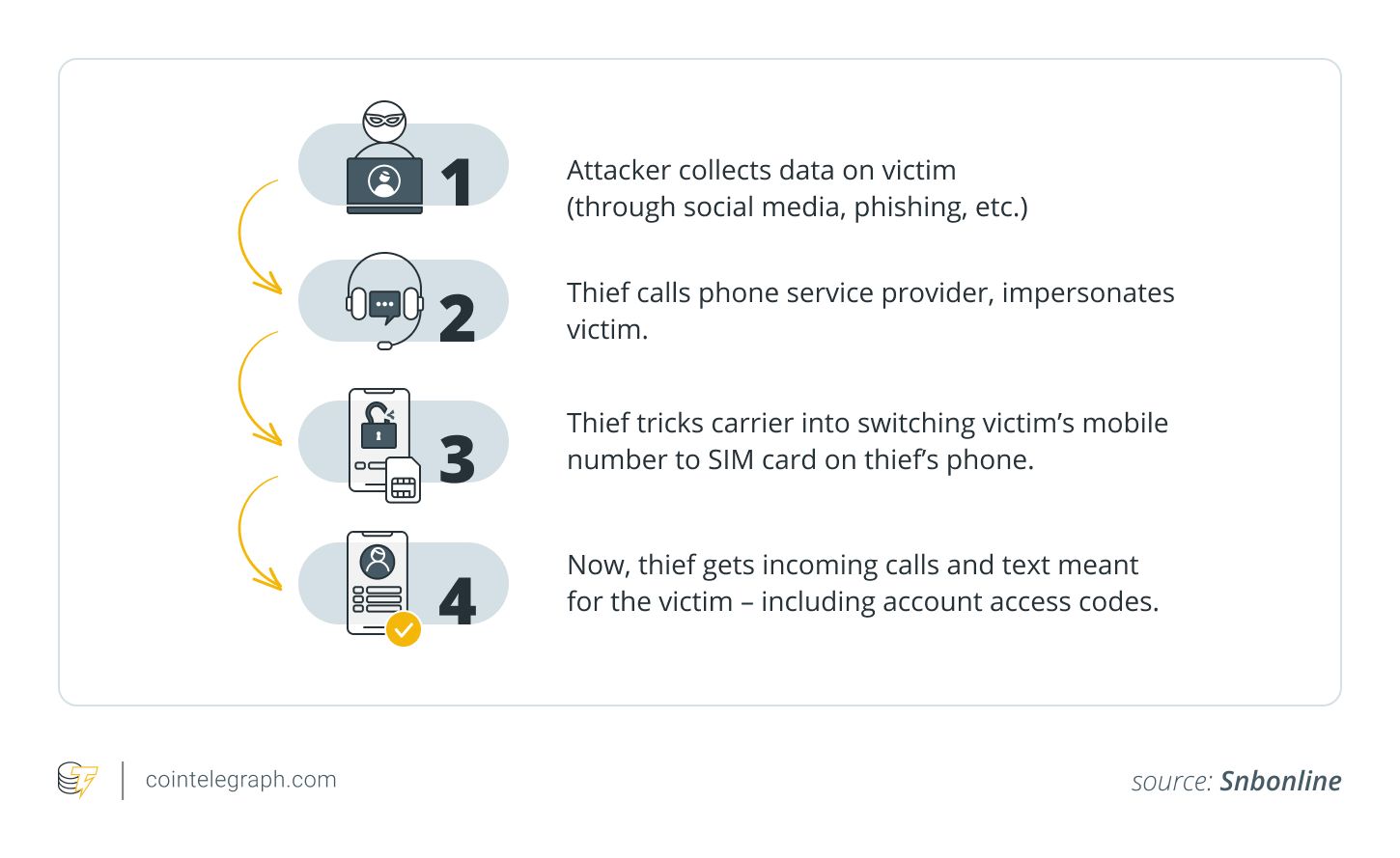
 ️ How SIM Swap Attacks Work
️ How SIM Swap Attacks WorkRecon: Scammers gather personal info via leaks, social media, or public records.
Impersonation: They call the victim’s carrier, posing as the account holder.
Execution: Carrier transfers the phone number to the attacker’s SIM card.
Impact: Scammers now receive all calls & SMS, including 2FA codes, giving them access to crypto, banking, and even email accounts.
Within minutes, funds can vanish.
One high-profile case: Brandon Buchanan, co-founder of Iterative Capital. After a SIM swap, attackers impersonated him and tricked an associate into sending $450K in Bitcoin.
 ️ Protecting Yourself Against SIM Swaps
️ Protecting Yourself Against SIM SwapsIndividuals:
Never rely on SMS-based 2FA. Use authenticator apps or, better, hardware security keys.
Use a dedicated phone number for 2FA (one not tied to your identity).
Create unique proxy emails for services to obscure your real one.
Regularly check for compromised accounts via haveibeenpwned.com
-
This is exactly why SMS 2FA should be considered obsolete in crypto. If your security relies on your phone carrier, you’re basically outsourcing your safety to a call center employee who can be tricked in 5 minutes.



















