🚨 North Korean Hackers Target Coinbase Jobs 🚨
-
1/
Coinbase, the #3 exchange by volume, is facing a new threat vector:
 DPRK IT workers applying as remote devs to infiltrate internal systems.
DPRK IT workers applying as remote devs to infiltrate internal systems.2/
CEO Brian Armstrong told the Cheeky Pint podcast:“Feels like 500 new people graduating every quarter from some kind of school… their whole job is stealing crypto.”
3/
Coinbase response:In-person US training required for staff.
Fingerprinting for those w/ sensitive access.
Only US citizens allowed to touch critical systems.
Basically: “remote first” isn’t safe when North Korea wants your hot wallet keys.
4/
Context:June 2024 → 4 NK operatives infiltrated multiple crypto startups as freelancers. Loot: $900K.
DPRK’s playbook = fake résumés + dev skills → infiltrate teams → drain funds.
5/
This comes after Coinbase’s May 2024 breach (1% of users hit, up to $400M losses).
Data leaked = addresses + balances → real-world physical danger.Arrington warns: “Hackers know where whales live. That’s the scary part.”
6/
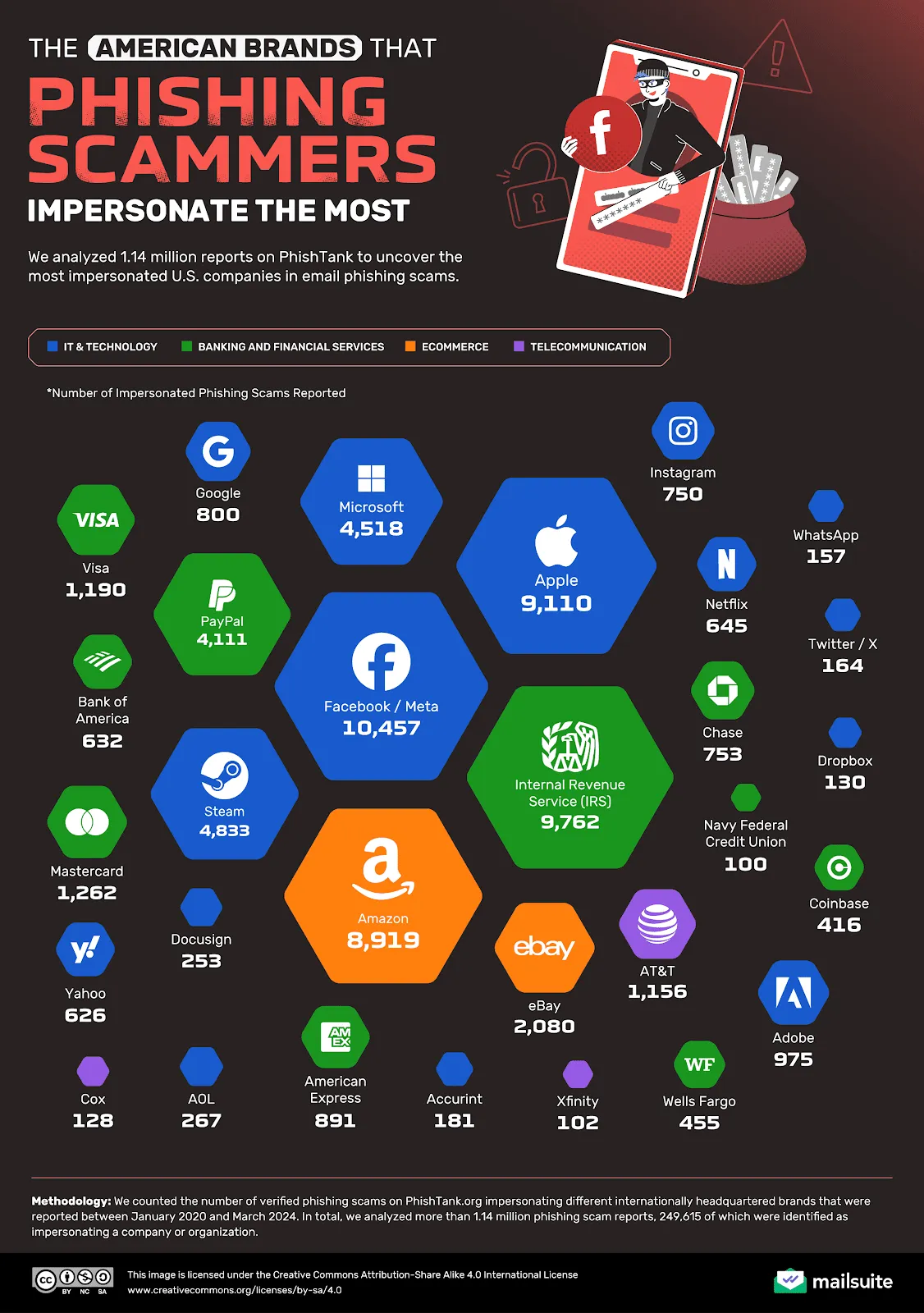
Coinbase also = most impersonated US crypto brand in phishing.416 phishing scams in last 4 years.
For comparison: Meta = 10,457 scams, IRS = 9,762.
7/
 Big Picture
Big PictureDPRK has weaponized labor markets as a crypto attack vector.
Nation-state actors view crypto firms as honey pots.
Web3 security ≠ just smart contracts → it’s HR, opsec, physical safety.
8/
 Takeaway: Coinbase tightening its remote policy is just the start.
Takeaway: Coinbase tightening its remote policy is just the start.
If you’re building in crypto → assume the adversary is a state with 500 fresh hackers every quarter. -
This is a chilling reminder that “security” isn’t just code audits and multisigs — it’s people. HR teams are now on the frontlines of cyberwarfare. Fake résumés with real skills are harder to filter than malware. Coinbase’s move to limit sensitive access to U.S. citizens may feel restrictive, but when you’re up against a nation-state farming thousands of trained operatives, zero-trust hiring becomes survival, not paranoia.
-
The scary part isn’t just the hot wallet keys — it’s the human layer. A $400M hack hurts, but leaked user addresses and balances = real-world risk. Imagine being a whale knowing DPRK-linked groups have your data. This shifts the conversation from “how do we protect funds?” to “how do we protect people?” Crypto companies need to harden opsec the same way governments protect classified info — because that’s what these digital treasuries effectively are.

















