🚨 North Korean IT Workers Infiltrate Crypto Projects via Fake IDs & Google Tools
-
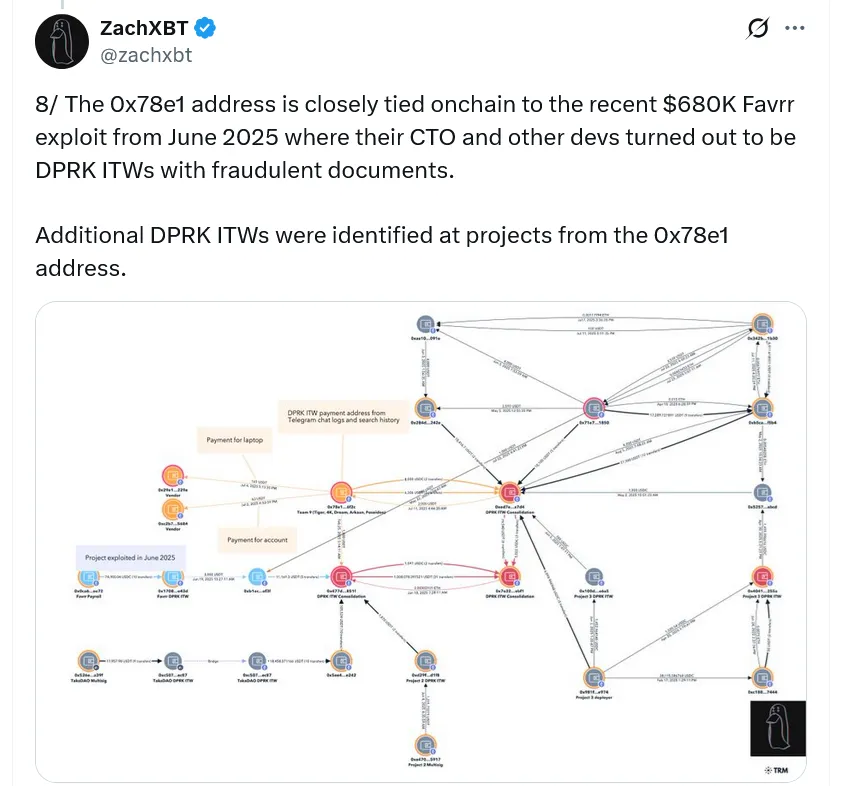
A small DPRK team linked to a $680K crypto hack in June has been exposed using fake identities, Google products, and freelance platforms to penetrate the Web3 industry.
 ️ Key findings (via @zachxbt):
️ Key findings (via @zachxbt):The six-person team used at least 31 fake identities with real government IDs, phone numbers, and purchased Upwork/LinkedIn accounts.
Posed as engineers from Polygon Labs, OpenSea, and Chainlink in scripted interviews.
Secured jobs on Upwork as blockchain devs, accessed companies using AnyDesk, VPNs, and Google tools for ops and comms.
Monthly expenses to run the op: $1,489 (as shown in internal docs).
Tied to $680K exploit on Favrr in June 2025 via wallet 0x78e1a.
Used Payoneer to convert fiat to crypto.
 Leaked docs show:
Leaked docs show:Interview prep docs.
Curiosity in AI firms and ERC-20 deployment on Solana.
Chrome profiles, Google Drive exports, and budget spreadsheets in English via translation tools.
🧠 Why it matters:
DPRK ops aren’t always sophisticated, just persistent.
Lax hiring and minimal due diligence = big vulnerabilities.
U.S. Treasury recently sanctioned multiple actors linked to similar rings.
 Takeaway for crypto orgs:
Takeaway for crypto orgs:
Stronger due diligence and better platform coordination are urgently needed. -
What stands out to me is how this DPRK team didn’t rely on ultra-sophisticated zero-day exploits — instead, they exploited human trust and weak verification processes. Fake LinkedIn/Upwork accounts, scripted interviews, and remote access tools like AnyDesk are not cutting-edge hacks, yet they still breached companies handling millions. This should be a wake-up call for Web3 firms to treat hiring pipelines as part of their security perimeter. Identity verification, multi-stage interviews, and background checks need to be standard, especially for remote dev roles with sensitive access.
-
This case highlights a huge vulnerability in the freelance economy — especially in crypto. Platforms like Upwork and LinkedIn are fantastic for finding talent, but they’re also perfect hunting grounds for nation-state actors who can blend in as skilled remote workers. Once inside, even with a small contract, they gain tools, credentials, and insider knowledge. It’s not just a blockchain problem; any remote-first tech company could be next. The industry desperately needs better collaboration between freelance platforms, security researchers, and hiring managers to flag suspicious patterns before these actors cash out with another $680K.

















