🚨 GreedyBear Crypto Scam Hits “Industrial Scale” — Over $1M Stolen
-
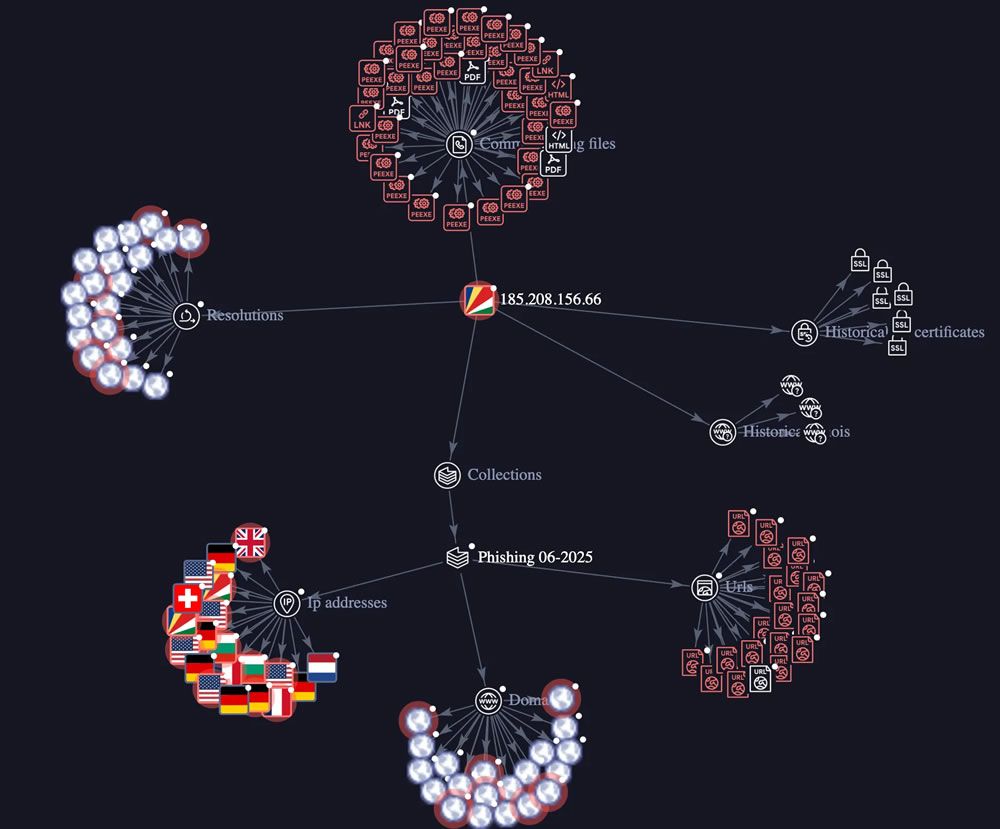
Cybersecurity firm Koi Security has exposed a massive crypto theft campaign by a cybercrime group dubbed GreedyBear, which has stolen over $1 million using a triple-threat strategy: fake wallet extensions, malware, and scam websites. What Makes GreedyBear Different?
What Makes GreedyBear Different?
Most criminal groups specialize in one scam method — GreedyBear is running all three at once and scaling like a business.1️⃣ Fake Wallet Extensions
150+ malicious add-ons on Firefox Marketplace. Impersonates popular wallets like MetaMask, TronLink, Exodus, Rabby Wallet. Uses “Extension Hollowing” — uploads a legit extension first, then swaps it for malicious code after approval. Steals wallet credentials directly from fake UI input fields.2️⃣ Crypto-Targeted Malware
Nearly 500 malware samples uncovered. Includes credential stealers like LummaStealer and ransomware like Luca Stealer. Spread mainly through Russian piracy/cracked software sites.3️⃣ Sophisticated Scam Websites
Fake landing pages for wallets, hardware devices, or “wallet repair” services. All coordinated from a single IP server hub for command-and-control and data theft. Why It’s Dangerous
Why It’s DangerousLeverages user trust in extension stores & positive reviews. Likely uses AI-generated code to scale attacks faster. Shows a shift toward multi-channel, industrialized crypto theft. Stay Safe
Stay SafeOnly install wallet extensions from verified sources. Double-check URLs — don’t trust ads or “sponsored” search results. Avoid downloading cracked software (common malware delivery method).#CryptoSecurity #GreedyBear #ScamAlert #WalletSecurity #DeFi

















