🚨 New Crypto Job Scam Drops Malware via "Mic Fix" Trick — Not PDFs
-
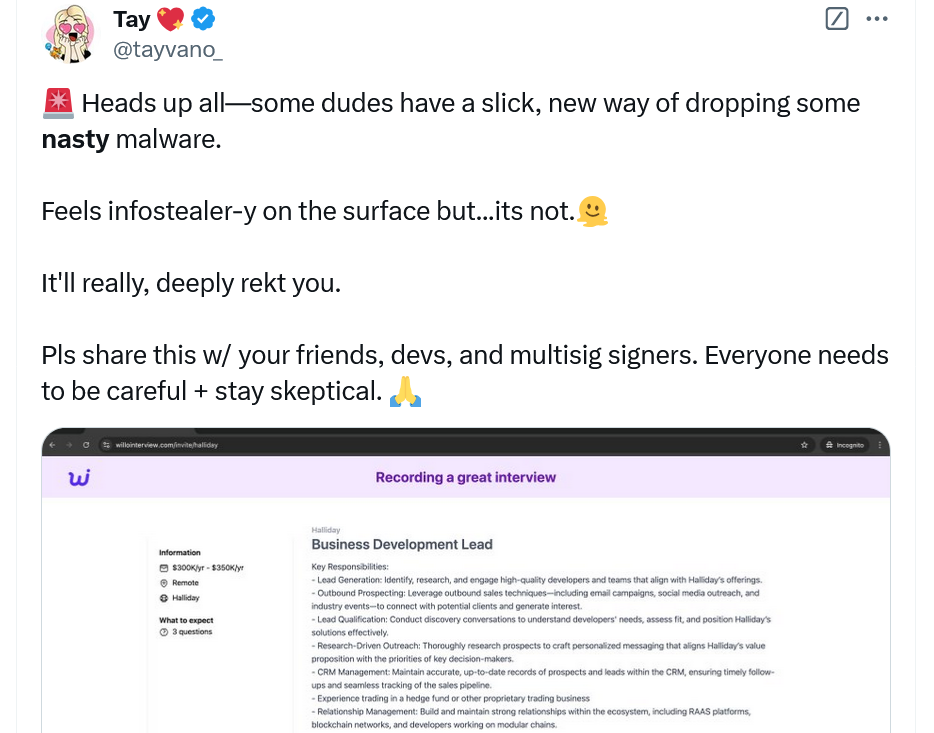
Scammers are back — but this time, they're skipping the fake PDFs and hitting you with something nastier.
According to blockchain sleuth Taylor Monahan (Tay), crypto hackers are running fake job interview scams targeting professionals on LinkedIn, Discord, Telegram, and freelancer sites.
 The setup:
The setup:You get approached for a “dream job” at a major crypto firm (Gemini, Kraken, etc.). They offer $200K–$350K for roles like BD, analyst, or researcher. After long interview Qs, you're asked to record a video response to a final question. Then comes the trap:
Then comes the trap:You’re told there’s a microphone/camera access issue (fake). They guide you to “fix it” — which actually triggers a malware install disguised as a Chrome update.🧨 Result?
Hackers get backdoor access to your device (Mac, Windows, Linux).
Once in, they can steal wallets, monitor activity, and completely wreck your system. ️ Warning Signs:
️ Warning Signs:Cold outreach with big salary offers Overly polished job descriptions Prompts to “fix” browser/device issues mid-interview Sudden Chrome update requests Tay’s advice:
Tay’s advice:
If you fell for this — wipe your device. Immediately.TL;DR:
Fake recruiters are no longer just after your résumé.
They're after your crypto — and this time, they brought backdoor malware disguised as "technical support."Stay skeptical. Stay safe.
 ️
️ -
 New scam alert: Forget fake PDFs — now scammers are dropping malware through fake “mic fix” tools during crypto job interviews.
New scam alert: Forget fake PDFs — now scammers are dropping malware through fake “mic fix” tools during crypto job interviews.
 Here’s how it works: You’re on a call, they say your mic isn’t working, then send you a link to "fix it." That file? It’s malware — designed to hijack your browser, steal wallet credentials, drain funds, and monitor everything you type.
Here’s how it works: You’re on a call, they say your mic isn’t working, then send you a link to "fix it." That file? It’s malware — designed to hijack your browser, steal wallet credentials, drain funds, and monitor everything you type.
🧠 If you’re job hunting in Web3, treat every file request like a red flag. Never download software from strangers. Use VMs, keep hot wallets separate, and verify every link. This isn’t paranoia — it’s survival. -
 ️ This new “mic fix” job scam is wild — and it’s targeting crypto professionals. Scammers aren’t using sketchy PDFs anymore. They’re pretending to be hiring managers, then pushing malware through fake troubleshooting tools.
️ This new “mic fix” job scam is wild — and it’s targeting crypto professionals. Scammers aren’t using sketchy PDFs anymore. They’re pretending to be hiring managers, then pushing malware through fake troubleshooting tools.
 It feels casual and urgent: “Hey, your mic isn’t working — just run this tool real quick.” But once you do, it’s game over. The malware steals browser data, passwords, extensions, and crypto wallet access.
It feels casual and urgent: “Hey, your mic isn’t working — just run this tool real quick.” But once you do, it’s game over. The malware steals browser data, passwords, extensions, and crypto wallet access.
 If you’re in crypto, assume everything is an attack vector. Interviews, files, links — all of it. In this space, basic trust = expensive mistakes.
If you’re in crypto, assume everything is an attack vector. Interviews, files, links — all of it. In this space, basic trust = expensive mistakes.

















